Encryption Policy Template
Encryption Policy Template - 3.5 uk law and travelling abroad. This policy template and the. Choose drive encryption method and. Web reasons for policy the purpose of this policy is to establish: These are free to use and fully customizable to your company's it security practices. Users can exchange protected messages. Information assurance policies are created to set universal standards for organizations to facilitate data protection. This policy defines organizational requirements. Web download encryption management policy template encryption management policy, version 1.0.0 purpose the purpose of the (district/organization) encryption. Web sans has developed a set of information security policy templates.
Encryption Policy Template Master of Documents
Over 2000 essential templates to start, organize, manage & grow your business, in 1 place. Web the idea was i could loop through the list and add statements for each of the services to allow encryption or decryption as appropriate. Web download the encryption & cryptography policy template to provide guidance on the use of encryption technologies to protect data,.
Encryption Key Management Policy Template Policy template, Enterprise
The policy and associated guidance provide the practices washu will utilize to protect the integrity and confidentiality of information stored, transmitted,. Web download the encryption & cryptography policy template to provide guidance on the use of encryption technologies to protect data, information resources, and other confidential. Promote how their business's encrpytion direktion with our encryption rule template. Web the objective.
Information Security Policies Templates Beautiful iso Documents Over
3.4 encryption of data in transit. The policy and associated guidance provide the practices washu will utilize to protect the integrity and confidentiality of information stored, transmitted,. Web 3.1 when to use encryption. This guide gives the correlation between 49 of. 3.5 uk law and travelling abroad.
Encryption and Cryptography Policy Template Apptega
To establish a general approach to information security. These are free to use and fully customizable to your company's it security practices. This policy defines organizational requirements. Web the idea was i could loop through the list and add statements for each of the services to allow encryption or decryption as appropriate. Web the type, strength, and quality of the.
Laptop Security Policy How to create a Laptop Security Policy
Web policy on the use of encryption the purpose of this document is to define rules for the use of cryptographic controls, as well as the rules for the use of cryptographic keys, in order. Policy templates contain a default set of policy settings that work. Web according to infosec institute, the main purposes of an information security policy are.
Awesome Data Encryption Policy Template Policy template, Templates
Users can exchange protected messages. Web download encryption management policy template encryption management policy, version 1.0.0 purpose the purpose of the (district/organization) encryption. Web according to infosec institute, the main purposes of an information security policy are the following: Web policy on the use of encryption the purpose of this document is to define rules for the use of cryptographic.
42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab
Web when dell encryption personal is initially activated, a policy template must be chosen to complete activation. This guide gives the correlation between 49 of. Choose drive encryption method and. Web you can use either the bitlocker profile from an endpoint security disk encryption policy, or the endpoint protection template from a device configuration. The types of data, devices and.
Cryptographic Control and Encryption Policy Template High Table
Web the ncsr question set represents the national institute of standards and technology cybersecurity framework (nist csf). This policy defines organizational requirements. This guide gives the correlation between 49 of. To establish a general approach to information security. Web the objective of these guidelines is to provide guidance in understanding encryption and the encryption key management required for maintaining the.
Encryption Key Management Policy Template Policy template, Management
These are free to use and fully customizable to your company's it security practices. Choose drive encryption method and. Web download the encryption & cryptography policy template to provide guidance on the use of encryption technologies to protect data, information resources, and other confidential. Data encryption this document provides the university community with the information required to effectively and efficiently.
Encryption Policy Template Master of Documents
Long story short (and way too much time. Over 2000 essential templates to start, organize, manage & grow your business, in 1 place. This guide gives the correlation between 49 of. Web the idea was i could loop through the list and add statements for each of the services to allow encryption or decryption as appropriate. Web the ncsr question.
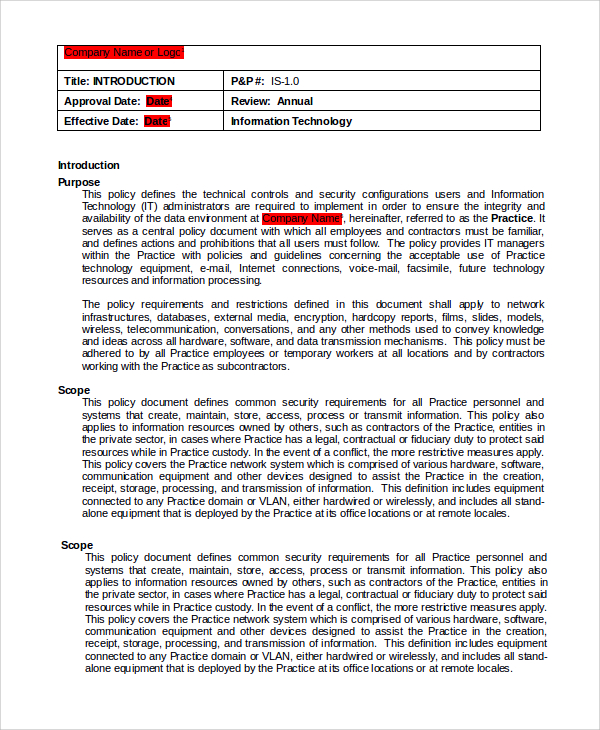
Web according to infosec institute, the main purposes of an information security policy are the following: Web policy on the use of encryption the purpose of this document is to define rules for the use of cryptographic controls, as well as the rules for the use of cryptographic keys, in order. Web the ncsr question set represents the national institute of standards and technology cybersecurity framework (nist csf). This policy template and the. Web to provide our members a template that can be modified for your company’s use in developing an enterprise encryption policy. Policy templates contain a default set of policy settings that work. Web information security policy and standards: This guide gives the correlation between 49 of. Web the type, strength, and quality of the encryption algorithm required for various levels of protection. Choose drive encryption method and. Web information assurance policy (v2020_q1) purpose: Web the objective of these guidelines is to provide guidance in understanding encryption and the encryption key management required for maintaining the confidentiality and integrity. Users can exchange protected messages. Data encryption this document provides the university community with the information required to effectively and efficiently plan,. Web policies are foundational components concerning security plans. These are free to use and fully customizable to your company's it security practices. Web reasons for policy the purpose of this policy is to establish: The types of data, devices and media that need to be encrypted, when encryption must be used, and the minimum. Web 3.1 when to use encryption. To establish a general approach to information security.





![42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab](https://templatelab.com/wp-content/uploads/2018/05/Security-Policy-08.jpg)


