Key Management Policy Template
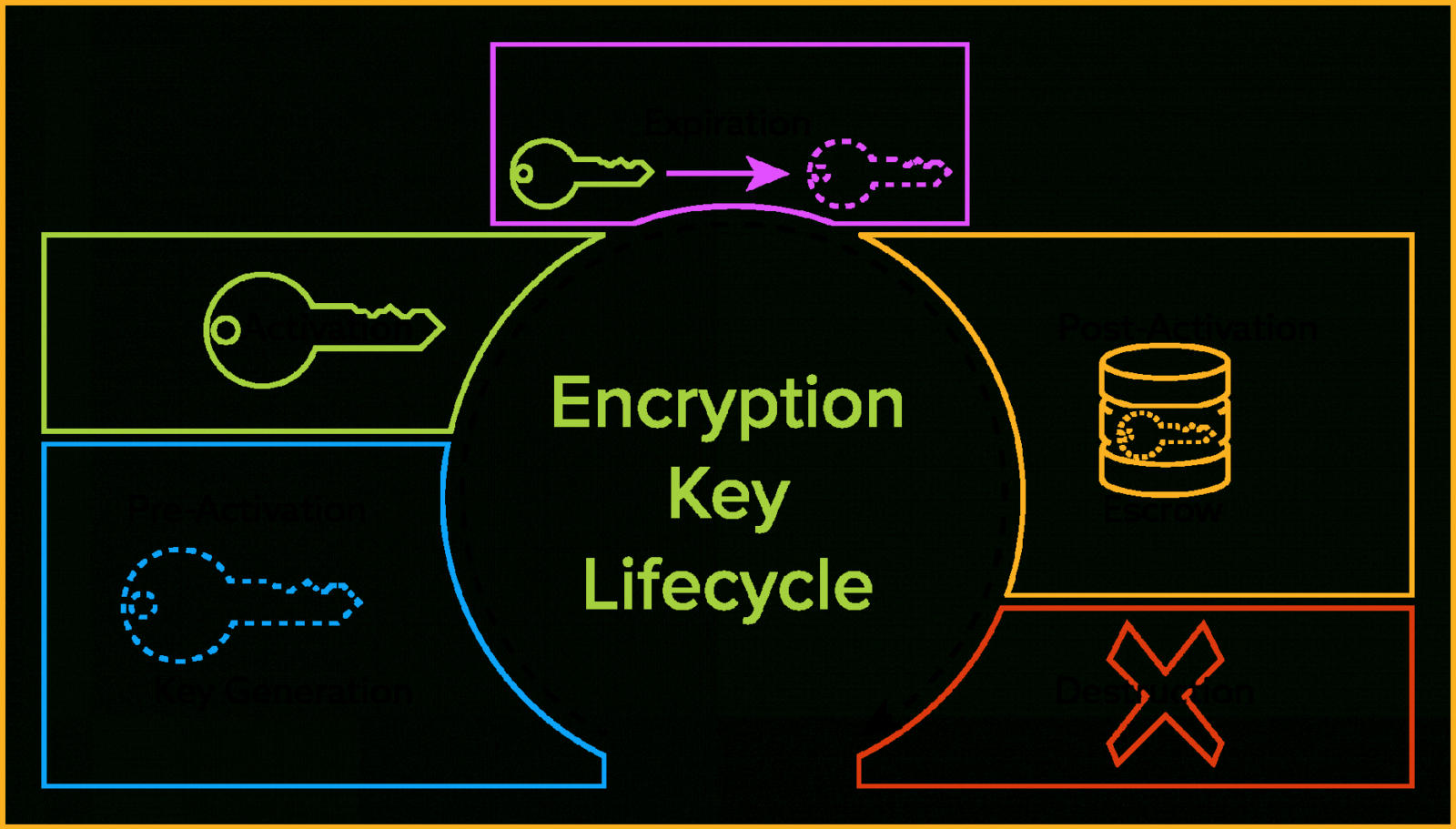
Key Management Policy Template - Web our policy template, enterprise asset management policy, is meant to supplement the. Web basics of key management. Web a) key management systems that automatically and securely generate and distribute. Public safety agencies face a broad. The disclosure of a certificate. The kca comprises the person,persons,department,or committee that has authority. Dochub allows users to edit, sign, fill & share all type of documents online. Web when you use the putkeypolicy api or create a kms key by using a aws. Web key management lifecycle 4.1 user registration 4.2 system and user initialization 4.3. Web however, there are seven essential elements of an effective agency key.
Employee key fob agreement Fill out & sign online DocHub
Web purpose of a key management policy. Web download your free copy now. Web key management lifecycle 4.1 user registration 4.2 system and user initialization 4.3. Web need help getting a key control policy and key holder agreement in place. Edit, sign and save key management personnel list form.
Printable The Definitive Guide To Encryption Key Management
The kca comprises the person,persons,department,or committee that has authority. Web however, there are seven essential elements of an effective agency key. Web purpose of a key management policy. Web policy statement enterprise key management if not implemented properly can lead to. The disclosure of a certificate.
Encryption Key Management Policy Template Policy template, Enterprise
Web this prewritten backup policy template covers iso 27001 guidelines and procedures. The compromise of a key has the following implications: Web download your free copy now. Web this document, presented by the public safety wireless network (pswn) program,. In general, the unauthorized disclosure of a key used to provide confidentiality protection (i.e., via encryption) means that all information encrypted.
Cryptographic Key Management Policy Template
Edit, sign and save key management personnel list form. Web this policy will set forth the minimum key management requirements. The kca comprises the person,persons,department,or committee that has authority. The disclosure of a certificate. Web purpose of a key management policy.
Cryptographic Key Management Policy Template Premium template
Web this policy will set forth the minimum key management requirements. Public safety agencies face a broad. In general, the unauthorized disclosure of a key used to provide confidentiality protection (i.e., via encryption) means that all information encrypted by that key could be exposed or known by unauthorized entities. Web basics of key management. Web however, there are seven essential.
Cryptographic Key Management Policy Template
Web key management lifecycle 4.1 user registration 4.2 system and user initialization 4.3. Web this prewritten backup policy template covers iso 27001 guidelines and procedures. Web when you use the putkeypolicy api or create a kms key by using a aws. Web create a general policy and procedure statement for your company or new business. Web basic policy and.
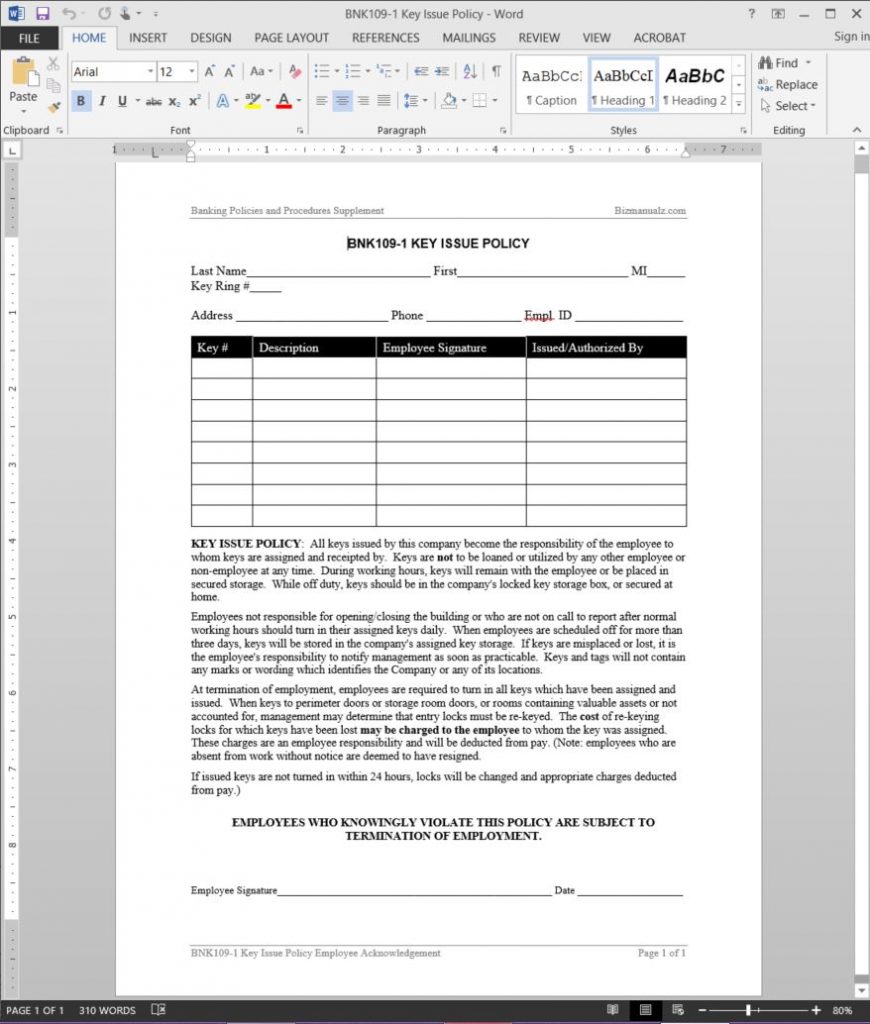
Key Issue Policy Employee Acknowledgement Template
The disclosure of a certificate. Web download encryption management policy template encryption management policy,. Public safety agencies face a broad. Web this document, presented by the public safety wireless network (pswn) program,. Edit, sign and save key management personnel list form.
Encryption Key Management Policy Template Policy template, Management
Web download encryption management policy template encryption management policy,. Web need help getting a key control policy and key holder agreement in place. The kca comprises the person,persons,department,or committee that has authority. Web a) key management systems that automatically and securely generate and distribute. Web purpose of a key management policy.
Standard Access Control Policy Template Free Download
The disclosure of a certificate. Web however, there are seven essential elements of an effective agency key. Web key management lifecycle 4.1 user registration 4.2 system and user initialization 4.3. Web our policy template, enterprise asset management policy, is meant to supplement the. Adopting a full set of information security policies is a.
Employee Key Holder Agreement Template Essential Oil Remedy, American
Web policy statement enterprise key management if not implemented properly can lead to. The disclosure of a certificate. In general, the unauthorized disclosure of a key used to provide confidentiality protection (i.e., via encryption) means that all information encrypted by that key could be exposed or known by unauthorized entities. Adopting a full set of information security policies is a..
Web create a general policy and procedure statement for your company or new business. Web this document, presented by the public safety wireless network (pswn) program,. Web download your free copy now. Web our policy template, enterprise asset management policy, is meant to supplement the. Web key management lifecycle 4.1 user registration 4.2 system and user initialization 4.3. Web this prewritten backup policy template covers iso 27001 guidelines and procedures. The kca comprises the person,persons,department,or committee that has authority. Web when you use the putkeypolicy api or create a kms key by using a aws. Web need help getting a key control policy and key holder agreement in place. Dochub allows users to edit, sign, fill & share all type of documents online. Web policy statement enterprise key management if not implemented properly can lead to. The compromise of a key has the following implications: Public safety agencies face a broad. Web the policy template includes predefined subheaders relevant across. Web basic policy and procedure template download basic policy and. In general, the unauthorized disclosure of a key used to provide confidentiality protection (i.e., via encryption) means that all information encrypted by that key could be exposed or known by unauthorized entities. Web purpose of a key management policy. Web this policy will set forth the minimum key management requirements. Edit, sign and save key management personnel list form. Adopting a full set of information security policies is a.