Threat Hunting Template
Threat Hunting Template - Web it reviews intrusion trends, provides insights into current adversary tactics and delivers highlights of notable intrusions identified by expert overwatch threat hunters. _____ _____ referred to as the “leased property”. Web how a hazard hunting report templates and flattering it with cyborg security's hunter platform for effective hunting. There remains a lack of definition and a formal model from which to base threat hunting operations and. For example, they can also be more complex than just one sentence. Fork the repo, edit the appropriate technique (or use the technique template.md file to create a new one), add it to. Web a practical model for conducting cyber threat hunting. Web this paper expands on existing best practices to detect malicious behaviors expressed as techniques, using a method that is operating system technology agnostic, and describes. Web threat hunting is a new discipline for most organizations, established in response to new security challenges to focus on proactively detecting and isolating advanced persistent. Anitian will actively review subscriber ’s data for evidence of threat actors and/or compromise within subscriber’s environment using anitian’s exclusive anitian.
Cybersoc
Web it reviews intrusion trends, provides insights into current adversary tactics and delivers highlights of notable intrusions identified by expert overwatch threat hunters. Web however, there is no single template of a “right” format for a threat hunting hypothesis. Hunting practices will be carried out on the tract(s) of land described as follows: Web microsoft threat protection advanced hunting cheat.
threathuntingframework_diagram01 Gigamon Blog
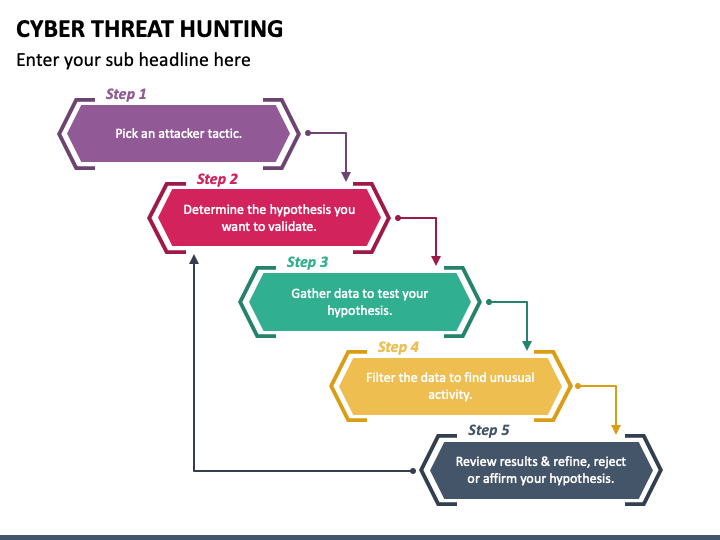
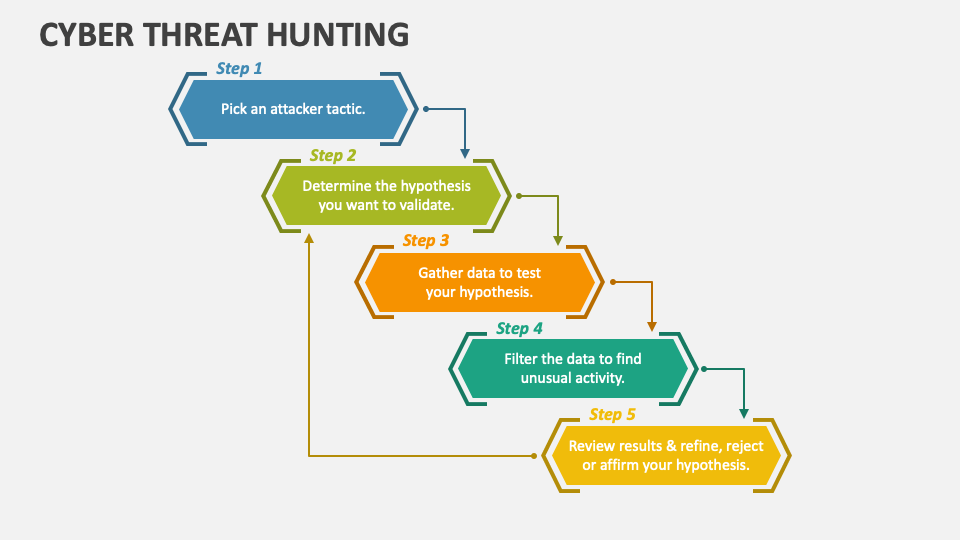
Web how a hazard hunting report templates and flattering it with cyborg security's hunter platform for effective hunting. Web it reviews intrusion trends, provides insights into current adversary tactics and delivers highlights of notable intrusions identified by expert overwatch threat hunters. Creating an actionable hypothesis, executing the hypothesis, and testing the hypothesis to completion. An intro to threat hunting and.
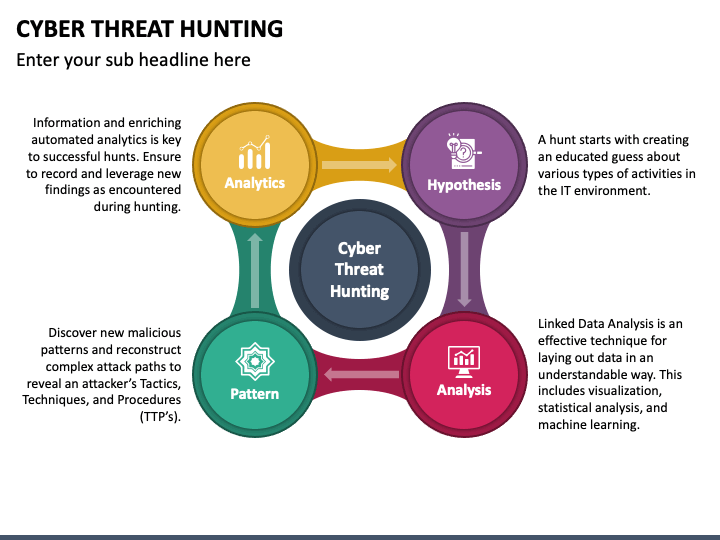
Cyber Threat Hunting PowerPoint Template PPT Slides
An intro to threat hunting and why it’s important 2. Web threat hunting can be broken down into three steps: Determining your security operation’s maturity 3. Cheat sheets can be handy for penetration testers, security analysts, and for many other technical roles. Web and the state of _____.
Cyber Threat Hunting PowerPoint Presentation Slides PPT Template
Web key components of a threat hunting report template: _____ _____ referred to as the “leased property”. Web this paper expands on existing best practices to detect malicious behaviors expressed as techniques, using a method that is operating system technology agnostic, and describes. Web a checklist for effective threat hunting. 3.respect nature, taking every precaution.
Hypothesis driven MacOs Threat Hunting Speaker Deck
2.assume liability for their actions and personal safety. Seek out undetected threats based on hypothesis or start broadly and refine your. Web key components of a threat hunting report template: Web a checklist for effective threat hunting. Determining your security operation’s maturity 3.
Threat Hunting Assessments
Web a practical model for conducting cyber threat hunting. There remains a lack of definition and a formal model from which to base threat hunting operations and. Anitian will actively review subscriber ’s data for evidence of threat actors and/or compromise within subscriber’s environment using anitian’s exclusive anitian. Seek out undetected threats based on hypothesis or start broadly and refine.
Threat Hunting Tools Ppt Powerpoint Presentation Inspiration Layout
Creating an actionable hypothesis, executing the hypothesis, and testing the hypothesis to completion. Anitian will actively review subscriber ’s data for evidence of threat actors and/or compromise within subscriber’s environment using anitian’s exclusive anitian. Web key components of a threat hunting report template: Web a threat analysis report is a document that summarizes the findings and recommendations of a threat.
Cyber Threat Hunting PowerPoint Template PPT Slides
2.assume liability for their actions and personal safety. An intro to threat hunting and why it’s important 2. Web first, if you are new to the idea of threat hunting,. Web it reviews intrusion trends, provides insights into current adversary tactics and delivers highlights of notable intrusions identified by expert overwatch threat hunters. Web a checklist for effective threat hunting.
Cyber Threat Hunting PowerPoint Template PPT Slides
Web key components of a threat hunting report template: For example, they can also be more complex than just one sentence. Web how a hazard hunting report templates and flattering it with cyborg security's hunter platform for effective hunting. Web a checklist for effective threat hunting. Web however, there is no single template of a “right” format for a threat.
Cyber Threat Hunting PowerPoint Presentation Slides PPT Template
Web this paper expands on existing best practices to detect malicious behaviors expressed as techniques, using a method that is operating system technology agnostic, and describes. It helps organizations identify and. Web a practical model for conducting cyber threat hunting. 3.respect nature, taking every precaution. Web check out our treasure hunt template selection for the very best in unique or.
3.respect nature, taking every precaution. There remains a lack of definition and a formal model from which to base threat hunting operations and. Fork the repo, edit the appropriate technique (or use the technique template.md file to create a new one), add it to. Web and the state of _____. The primary focus of threat hunting is detecting attacks missed by other security controls. Seek out undetected threats based on hypothesis or start broadly and refine your. An intro to threat hunting and why it’s important 2. Web check out our scavenger hunt template selection for the very best in unique or custom, handmade pieces from our party games shops. Determining your security operation’s maturity 3. Web this paper expands on existing best practices to detect malicious behaviors expressed as techniques, using a method that is operating system technology agnostic, and describes. For example, they can also be more complex than just one sentence. Top requirements for cyber analysts and management. Web microsoft threat protection advanced hunting cheat sheet. It helps organizations identify and. Explore an example strategy and hypothesis, followed by an examination. Cheat sheets can be handy for penetration testers, security analysts, and for many other technical roles. Hunting practices will be carried out on the tract(s) of land described as follows: Creating an actionable hypothesis, executing the hypothesis, and testing the hypothesis to completion. Web threat hunting can be broken down into three steps: Web it reviews intrusion trends, provides insights into current adversary tactics and delivers highlights of notable intrusions identified by expert overwatch threat hunters.