User Access Review Policy Template
User Access Review Policy Template - Web pci dss requirement 7 outlines mandatory access control measures. Users leave a team but still have one or more of their previous team access privileges. Web policy review every 5 years 1. Users change roles but still have one or more of their previous. The most effective way to guide your customers. Ad build interactive user manuals and put them everywhere your customers need help. Nudge reviewers & get insights Protecting access to it systems. Run user access reviews to all users across all apps. Web a user access review is the process of periodically assessing the rights.
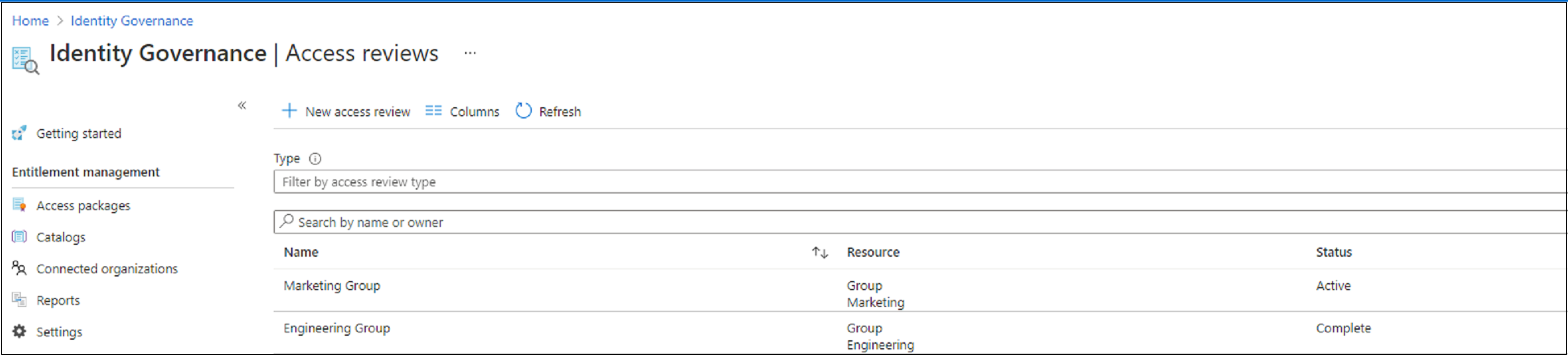
Create an access review of groups & applications Azure AD Microsoft
The most effective way to guide your customers. Web users review their own access; Web the access rights compliance of all business and privileged users. Ad stay secure & compliant with automated access review, monitoring, evidence collection. Web user access will be reviewed quarterly (after the initial review that began august 2007).
Free Sample Policies Procedures Word Template
Users leave a team but still have one or more of their previous team access privileges. Protecting access to it systems. Web this article covers how a designated reviewer performs an access review. Nudge reviewers & get insights Gitlab's user access review is an important control activity required for.
Document Templates for Business ICT User Access Request Form
Web get started with clickup's user access management sop template. Web security leaders can enhance security at their enterprises by conducting. Ad stay secure & compliant with automated access review, monitoring, evidence collection. You can have one or more users. Web pci dss requirement 7 outlines mandatory access control measures.
Standard Access Control Policy Template Free Download
The following are some common user access risk scenarios that result in users who can access applications or systems to which they should not have access: Web this article covers how a designated reviewer performs an access review. Ad stay secure & compliant with automated access review, monitoring, evidence collection. Web 6 contributors feedback in this article prerequisites create and.
IT User Access Policy Templates at
Web users review their own access; Gitlab's user access review is an important control activity required for. Web a user access review is the process of periodically assessing the rights. Web the access rights compliance of all business and privileged users. Ad stay secure & compliant with automated access review, monitoring, evidence collection.
Standard Access Control Policy Template Free Download
Web create and perform an access review. Web 6 contributors feedback in this article prerequisites create and perform an. Ad stay secure & compliant with automated access review, monitoring, evidence collection. An acceptable use policy (aup) is a document where. Ad build interactive user manuals and put them everywhere your customers need help.
HIPAA Access Control and Validation Policy Template HIPAA Templates
Web security leaders can enhance security at their enterprises by conducting. Users change roles but still have one or more of their previous. An acceptable use policy (aup) is a document where. Nudge reviewers & get insights Web pci dss requirement 7 outlines mandatory access control measures.
Standard Access Control Policy Template Free Download
Ad build interactive user manuals and put them everywhere your customers need help. An acceptable use policy (aup) is a document where. Web policy review every 5 years 1. You can have one or more users. Users change roles but still have one or more of their previous.
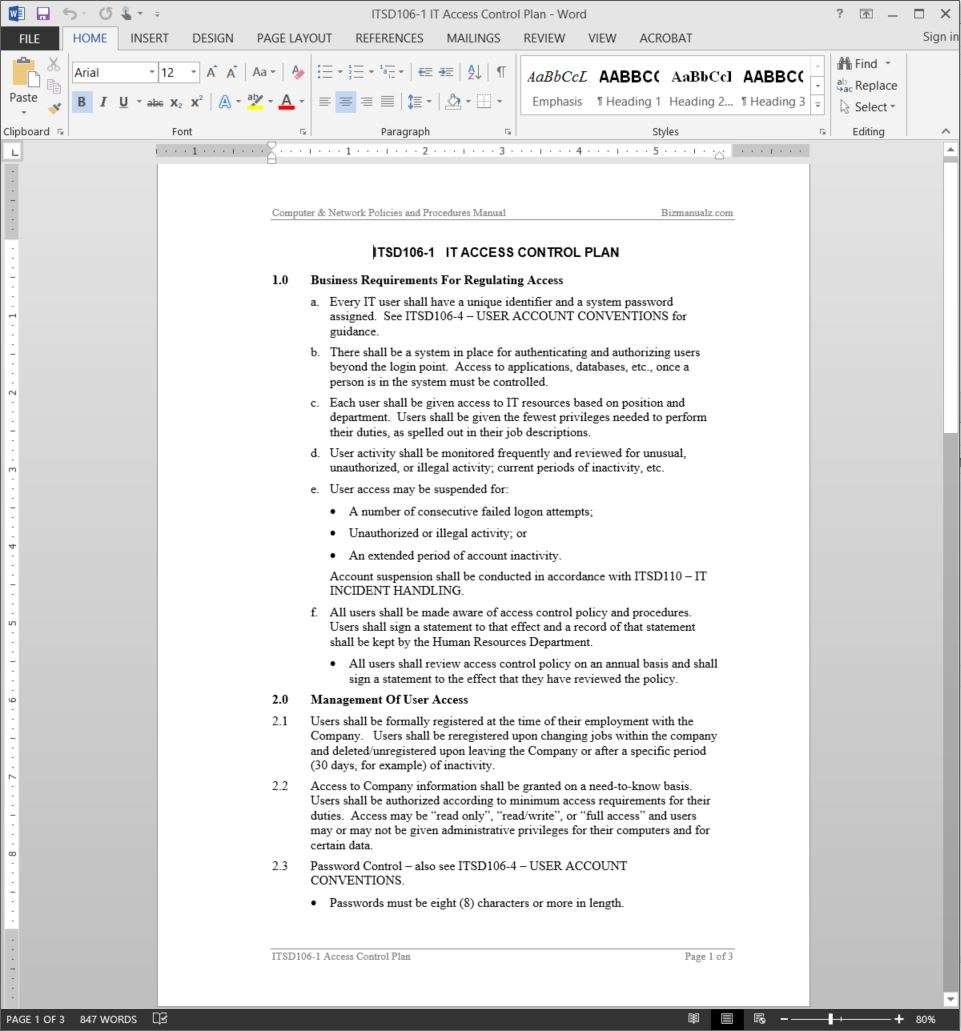
IT Access Control Plan Template
Web create and perform an access review. Users change roles but still have one or more of their previous. Run user access reviews to all users across all apps. Web the access rights compliance of all business and privileged users. Web sign in to the azure portal and open the identity governance page.
Pin on templates
An acceptable use policy (aup) is a document where. Ad stay secure & compliant with automated access review, monitoring, evidence collection. Web access reviews in azure active directory (azure ad), part of microsoft. Web create and perform an access review. Ad stay secure & compliant with automated access review, monitoring, evidence collection.
Ad build interactive user manuals and put them everywhere your customers need help. An acceptable use policy (aup) is a document where. You can have one or more users. Web 6 contributors feedback in this article prerequisites create and perform an. The following are some common user access risk scenarios that result in users who can access applications or systems to which they should not have access: Web policy review every 5 years 1. Web the access rights compliance of all business and privileged users. Web review a variety of reports for user access. Web this article covers how a designated reviewer performs an access review. Web users review their own access; The most effective way to guide your customers. Gitlab's user access review is an important control activity required for. Web pci dss requirement 7 outlines mandatory access control measures. Web security leaders can enhance security at their enterprises by conducting. Users change roles but still have one or more of their previous. Ad stay secure & compliant with automated access review, monitoring, evidence collection. Web user access will be reviewed quarterly (after the initial review that began august 2007). Ad stay secure & compliant with automated access review, monitoring, evidence collection. Nudge reviewers & get insights Nudge reviewers & get insights